折腾搬瓦工–09–为iPhone配置证书认证的VPN
文章目录
这次相比之前的配置增加了IKEv2证书认证登录,自用的配置也做了一些修改,鉴于之前的太零散,这次会完整记录所有配置过程。完整的配置脚本放在了GitHub上:IPSecAndIKEv2VPNWithStrongswan
这一篇的内容会比较多,因为VPN本身涉及的东西就非常多,这里总结下配置VPN直到现在的一些东西。如果是安卓用户或者iPhone越狱用户,推荐使用shadowsocks,但如果关心连接的安全性,或者无法使用shadowsocks,那么可以继续往下看。
VPS
你需要一台可以正常连接的VPS,搬瓦工,DigitalOcean,Vultr都是不错的选择,以深圳地区为例,使用traceroute跟踪,基本上的网络路线都是:深圳->广东省->电信骨干->上海->香港->电信美国出口->VPS,其中耗时最大的就是从香港到电信美国出口的,一般在150ms左右,而从本地网络到国内网络出口的时间基本在15ms左右。所以VPS的最佳选择是在香港或者日本等邻国,且网络线路可以直通,此外一般VPS都选择在美国西海岸的机房(本站就是),当然不排除一些地区能够直通其他国外的冷门路线。
现在的VPS已经没有便宜的了,搬瓦工上的性价比存货基本被扫光,目前最低配置为2.99美金/月,10GB SSD,256MB RAM,128MB vSwap,500GB Transter,不过全年的话,只要20美金,缺点是openVZ虚拟化,无法更改内核与交换空间,内核还停留在2.6。而DigitalOcean与Vultr目前的最低配置为5美金/月,前者为20GB SSD,512 MB RAM,后者为15GB SSD,768MB SSD,此外同样为KVM虚拟化,1TB流量,可以自行更改内核与交换空间,目前Vultr正在做活动,注册后,支付10美金,赠送20美金。对于这两家的美国西海岸机房,相对国内网络环境基本没有太大差别。
注册邀请码:
搬瓦工:https://bandwagonhost.com/aff.php?aff=4828
Vultr:http://www.vultr.com/?ref=6931403-3B
Vultr日本节点Ping测试
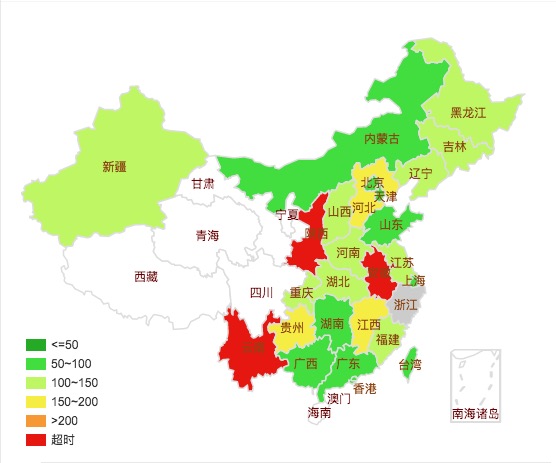
可以看到对于不同地区ping值差异还是很大的,同一个地区的不同运营商的差异也很大。所以只能找合适的VPS了,而且部分地区对于SS的检测力度提升,在我目前的网络环境下,连接速率SS比IKEv2慢约30%左右,不过我已经将梯子全部都搬到Vultr上,毕竟没有跨太平洋,速度还是十分感人的,只是在公司的时候ping值基本保持在70ms一下,而在家时就蹦上160ms,差异实在太大了。
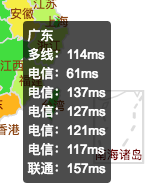
VPS配置
设备连接VPS并通过代理上网时,需要经过连接认证、分配虚拟IP、数据包的转发与接收。而VPN有很多种,但推荐使用IKEv2,其次是IKEv1(也可以认为是Cisco IPSec),其余的包括L2TP,PPTP等不再讨论范围内。经过测试,支持IKEv2协议的系统都可以使用,包括windows 7及以上,安卓和iOS 9以上,macOS 10.11及以上,如果无法使用IKEv2,也可以采用IKEv1(IPsec)。
1. 启用IPv4转发
检查启用状态
1cat /proc/sys/net/ipv4/ip_forward
输出为1则已启用,输出为0的话,编辑 /etc/sysctl.conf,搜索 net.ipv4.ip_forward=1,去除注释后保存,执行命令,启用转发。
1sysctl -p
2.strongSwan
(1)安装编译工具
1apt-get install build-essential libgmp3-dev libgmp-dev openssl libssl-dev -y
(2)下载、解压strongSwan
strongSwan最新版本可以在这里找到:strongSwan-downlaod
1wget https://download.strongswan.org/strongswan-5.5.0.tar.gz
2tar zxvf strongswan-5.5.0.tar.gz
(3)生成 Makefile
strongSwan的详细选项可以在这里找到:Autoconf
或者可以进入strongswan-5.5.0目录,执行命令查看
1./configure --help
官方文档中,基本所有的选项的默认配置都是no,所以可以尝试启用最基本的配置,即不带任何选项的./configure命令,来看看到底会启用哪些东西
1strongSwan will be built with the following plugins
2-----------------------------------------------------
3libstrongswan: aes des rc2 sha2 sha1 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey pem fips-prf gmp xcbc cmac hmac
4libcharon: attr kernel-netlink resolve socket-default stroke vici updown xauth-generic
5libtnccs:
默认选项中除了libstrongswan中的加密模块外,libcharon中还包括了xauth-generic,采用默认选项的话,基本所有支持IPSec VPN的设备都可以使用了,但不同设备、系统支持的认证方式不同,iOS上IKEv2 VPN默认验证方式为eap-mschapv2,证书认证可以使用eat-tls,对于无法使用IKEv2的系统版本,可以使用IPSec VPN。iOS具体支持的VPN类型可以参考苹果官方文档:https://help.apple.com/deployment/ios/#/apd1775f8cbb
配置后,编译并安装。
1./configure --sysconfdir=/etc --enable-eap-mschapv2 --enable-eap-identity --enable-md4 --enable-eap-tls
2make && make install
需要注意的是,如果VPS采用openVZ方案,一般内核都是2.6,不包含ipsec模块,需要增加一个配置选项:-enable-kernel-libipsec,kvm主机的内核一般在3.0以上,不需要再编译该模块。
1./configure --sysconfdir=/etc --enable-eap-mschapv2 --enable-eap-identity --enable-md4 --enable-eap-tls --enable-kernel-libipsec
(4)证书配置
如果要使用IKEv2的话,证书是绕不过的一道坎。客户端使用 根证书 与服务端发送过来的 服务器证书验证服务端,而服务端使用预设的账号密码或 客户端证书来验证客户端,但在认证完成后,服务端、客户端间的通信加密是一样的。
采用eap-mschapv2认证方式只需要安装根证书,配合账号、密码使用,而如果需要客户端也采用证书,可以使用eap-tls认证。
接下里涉及的一些选项不再做详细解释,具体文档可以查看官方文档:IpsecPKI
现在假定
服务器IP地址为:192.241.216.55
服务器IP对应域名为:ikev2.wbuntu.me
共有三份证书+私钥,分别是根证书,服务器证书,客户端证书。
1)生成根证书
1ipsec pki --gen --outform pem > caKey.pem
2ipsec pki --self --in caKey.pem --dn "C=CH, O=Wbuntu, CN=Wbuntu CA" --ca --outform pem > caCert.pem
2)生成服务端证书
1ipsec pki --gen --outform pem > serverKey.pem
2ipsec pki --pub --in serverKey.pem | ipsec pki --issue --cacert caCert.pem --cakey caKey.pem --dn "C=CH, O=Wbuntu, CN=ikev2.wbuntu.me" --san="ikev2.wbuntu.me" --flag serverAuth --outform pem > serverCert.pem
3)生成客户端证书
1ipsec pki --gen --outform pem > clientKey.pem
2ipsec pki --pub --in clientKey.pem | ipsec pki --issue --cacert caCert.pem --cakey caKey.pem --dn "C=CH, O=Wbuntu, CN=client.wbuntu.me" --san="client.wbuntu.me" --flag clientAuth --outform pem > clientCert.pem
此外客户端证书还需要转为p12格式,供iPhone使用
1openssl pkcs12 -export -inkey clientKey.pem -in clientCert.pem -name "client.wbuntu.me" -certfile caCert.pem -caname "Wbuntu CA" -out clientCert.p12
转换时提示需要输入密码,在客户端上安装证书时,会使用到这个密码。
现在,我们一共有七个文件分别是:
1caCert.pem caKey.pem clientCert.p12 clientCert.pem clientKey.pem serverCert.pem serverKey.pem
将以下文件复制到对应文件夹中,strongswan会在启动时读取。
1cp caCert.pem /etc/ipsec.d/cacerts/
2cp serverCert.pem /etc/ipsec.d/certs/
3cp serverKey.pem /etc/ipsec.d/private/
4cp clientCert.pem /etc/ipsec.d/certs/
5cp clientKey.pem /etc/ipsec.d/private/
(5)strongswan及ipsec配置
编辑 /etc/strongswan.conf,内容如下
1charon {
2 duplicheck.enable = no
3 install_virtual_ip = yes
4 dns1 = 8.8.8.8
5 dns2 = 8.8.4.4
6 load_modular = yes
7 plugins {
8 include strongswan.d/charon/*.conf
9 }
10}
11include strongswan.d/*.conf
编辑 /etc/ipsec.conf,内容如下
1config setup
2 uniqueids=never
3conn %default
4 ikelifetime=60m
5 keylife=20m
6 rekeymargin=3m
7 keyingtries=1
8 keyexchange=ike
9conn ikev1
10 keyexchange=ikev1
11 authby=xauthpsk
12 xauth=server
13 left=%defaultroute
14 leftsubnet=0.0.0.0/0
15 leftfirewall=yes
16 right=%any
17 rightsourceip=10.0.0.0/24
18 auto=add
19conn ikev2-eap-mschapv2
20 keyexchange=ikev2
21 leftauth=pubkey
22 leftcert=serverCert.pem
23 [email protected]
24 leftsendcert=always
25 left=%defaultroute
26 leftsubnet=0.0.0.0/0
27 leftfirewall=yes
28 rightauth=eap-mschapv2
29 right=%any
30 rightsourceip=10.0.0.0/24
31 eap_identity=%any
32 auto=add
33conn ikev2-eap-tls
34 keyexchange=ikev2
35 leftauth=pubkey
36 leftcert=serverCert.pem
37 [email protected]
38 leftsendcert=always
39 left=%defaultroute
40 leftsubnet=0.0.0.0/0
41 leftfirewall=yes
42 rightauth=eap-tls
43 rightcert=clientCert.pem
44 [email protected]
45 rightsourceip=10.0.0.0/24
46 eap_identity=%any
47 auto=add
注意 leftid 对应服务端证书中的CN, rightid 对应客户端证书中的CN,它们分别对应iOS的IKEv2 VPN中的 Remote Identifier 与 Local Identifier。必需是URL形式,之前测试过直接使用服务器IP来生成证书,配置ipse.conf,但在连接时都失败了。
编辑 /etc/ipsec.secrets,内容如下
1: RSA serverKey.pem
2: RSA clientKey.pem
3: PSK "tHcvZiJNucjL8"
4wbuntu : EAP "RKwQ1wV1m9Bsucks"
5wbuntu : XAUTH "RKwQ1wV1m9Bsucks"
头两行指定了用于解密公钥加密的私钥,第三行指定了IPSec VPN的预共享密钥,冒号左侧不指定用户,表示适用于所有的用户。
第四、五行配置了用户和登录密码,其中EAP对应的是使用EAP认证协议的用户,包括eap-mschapv2,eat-tls等;XAUTH对应使用IPSec VPN的用户,同一个用户名可以使用不同的协议登录。
(6)防火墙配置
防火墙使用iptables命令来配置。需要开放500,4500端口接收UDP数据包,允许防火墙接收esp包(IKEv2使用AH+ESP来认证封装载荷),最后需要转发ipsec.conf中配置的子网数据包,并在发送前,将数据包源IP改写为VPS的IP。所有命令如下。注意最后一条中,需要把IP地址替换为自己VPS的IP。
1iptables -A INPUT -p udp --dport 500 -j ACCEPT
2iptables -A INPUT -p udp --dport 4500 -j ACCEPT
3iptables -A INPUT -p esp -j ACCEPT
4iptables -A FORWARD -s 10.0.0.0/24 -j ACCEPT
5iptables -t nat -A POSTROUTING -s 10.0.0.0/24 -j SNAT --to-source 192.241.216.55
其中最后一条也可以改写为(kvm的VPS网卡一般都是eth0,可以用ifconfig命令查看后,然后自行替换)
1iptables -t nat -A POSTROUTING -s 10.0.0.0/24 -o eth0 -j MASQUERADE
对于IP不固定的VPS来说,需要每次在转发前,根据网卡的IP来改写数据包中的IP,不过对于固定IP的VPS,最好不要使用这个写法,因为会增加服务器压力(虽然用户较小时,压力不是很大)。
关于iptables的详细用法,可以参考这份文档:iptables 指南 1.1.19
同样,为了保证机子重启后,还可以保存规则,可以将它们存储在文件中,在重启后恢复。
1iptables-save > /etc/iptables.rules
2
3cat > /etc/network/if-up.d/iptables<<EOF
4#!/bin/sh
5iptables-restore < /etc/iptables.rules
6ipsec start
7EOF
8
9chmod +x /etc/network/if-up.d/iptables
现在可以启用VPN了
(7)调试
使用ipsec命令启用VPN服务
1#后台运行命令
2ipsec start
3#前提运行命令,用于调试
4ipsec start --nofork
5#停止命令
6ipsec stop
下面分别是在iOS 9上的配置与连接日志。
服务端: iptables-save 输出
1# Generated by iptables-save v1.6.0 on Sun Aug 7 02:17:05 2016
2*nat
3:PREROUTING ACCEPT [2102:147369]
4:INPUT ACCEPT [1657:118769]
5:OUTPUT ACCEPT [46:3239]
6:POSTROUTING ACCEPT [46:3239]
7-A POSTROUTING -s 10.0.0.0/24 -j SNAT --to-source 192.241.216.55
8COMMIT
9# Completed on Sun Aug 7 02:17:05 2016
10# Generated by iptables-save v1.6.0 on Sun Aug 7 02:17:05 2016
11*filter
12:INPUT ACCEPT [1334630:54714672]
13:FORWARD ACCEPT [0:0]
14:OUTPUT ACCEPT [445427:1940087014]
15-A INPUT -p esp -j ACCEPT
16-A INPUT -p udp -m udp --dport 500 -j ACCEPT
17-A INPUT -p udp -m udp --dport 4500 -j ACCEPT
18-A FORWARD -s 10.0.0.0/24 -j ACCEPT
19COMMIT
20# Completed on Sun Aug 7 02:17:05 2016
ipsec start --nofork 输出
1Starting strongSwan 5.5.0 IPsec [starter]...
200[DMN] Starting IKE charon daemon (strongSwan 5.5.0, Linux 4.4.0-31-generic, i686)
300[CFG] loading ca certificates from '/etc/ipsec.d/cacerts'
400[CFG] loaded ca certificate "C=CH, O=Wbuntu, CN=Wbuntu CA" from '/etc/ipsec.d/cacerts/caCert.pem'
500[CFG] loading aa certificates from '/etc/ipsec.d/aacerts'
600[CFG] loading ocsp signer certificates from '/etc/ipsec.d/ocspcerts'
700[CFG] loading attribute certificates from '/etc/ipsec.d/acerts'
800[CFG] loading crls from '/etc/ipsec.d/crls'
900[CFG] loading secrets from '/etc/ipsec.secrets'
1000[CFG] loaded RSA private key from '/etc/ipsec.d/private/serverKey.pem'
1100[CFG] loaded RSA private key from '/etc/ipsec.d/private/clientKey.pem'
1200[CFG] loaded IKE secret for %any
1300[CFG] loaded EAP secret for wbuntu
1400[CFG] loaded EAP secret for wbuntu
1500[LIB] loaded plugins: charon aes des rc2 sha2 sha1 md4 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey pem fips-prf gmp xcbc cmac hmac attr kernel-netlink resolve socket-default stroke vici updown eap-identity eap-mschapv2 eap-tls xauth-generic
1600[JOB] spawning 16 worker threads
17charon (2082) started after 80 ms
1805[CFG] received stroke: add connection 'ikev1'
1905[CFG] adding virtual IP address pool 10.0.0.0/24
2005[CFG] added configuration 'ikev1'
2110[CFG] received stroke: add connection 'ikev2-eap-mschapv2'
2210[CFG] reusing virtual IP address pool 10.0.0.0/24
2310[CFG] loaded certificate "C=CH, O=Wbuntu, CN=ikev2.wbuntu.me" from 'serverCert.pem'
2410[CFG] added configuration 'ikev2-eap-mschapv2'
2516[CFG] received stroke: add connection 'ikev2-eap-tls'
2616[CFG] reusing virtual IP address pool 10.0.0.0/24
2716[CFG] loaded certificate "C=CH, O=Wbuntu, CN=ikev2.wbuntu.me" from 'serverCert.pem'
2816[CFG] loaded certificate "C=CH, O=Wbuntu, CN=client.wbuntu.me" from 'clientCert.pem'
2916[CFG] added configuration 'ikev2-eap-tls'
客户端需要先安装caCert.pem以及clientCert.p12(这个文件需要输入之前设置的密码),可以将这两个文件放在Nginx网页目录下,用Safari访问文件进行安装。安装后如下所示:

1)IPSec VPN
客户端配置
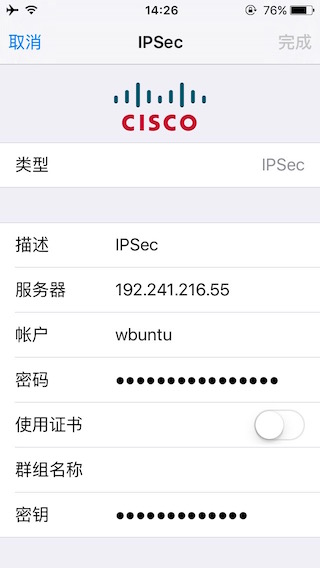
其中密码为账户对应密码,密钥为设定的PSK
服务端连接日志
113[NET] received packet: from 202.104.136.206[32783] to 192.241.216.55[500] (848 bytes)
213[ENC] parsed ID_PROT request 0 [ SA V V V V V V V V V V V V V V ]
313[IKE] received NAT-T (RFC 3947) vendor ID
413[IKE] received draft-ietf-ipsec-nat-t-ike vendor ID
513[IKE] received draft-ietf-ipsec-nat-t-ike-08 vendor ID
613[IKE] received draft-ietf-ipsec-nat-t-ike-07 vendor ID
713[IKE] received draft-ietf-ipsec-nat-t-ike-06 vendor ID
813[IKE] received draft-ietf-ipsec-nat-t-ike-05 vendor ID
913[IKE] received draft-ietf-ipsec-nat-t-ike-04 vendor ID
1013[IKE] received draft-ietf-ipsec-nat-t-ike-03 vendor ID
1113[IKE] received draft-ietf-ipsec-nat-t-ike-02 vendor ID
1213[IKE] received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
1313[IKE] received XAuth vendor ID
1413[IKE] received Cisco Unity vendor ID
1513[IKE] received FRAGMENTATION vendor ID
1613[IKE] received DPD vendor ID
1713[IKE] 202.104.136.206 is initiating a Main Mode IKE_SA
1813[ENC] generating ID_PROT response 0 [ SA V V V ]
1913[NET] sending packet: from 192.241.216.55[500] to 202.104.136.206[32783] (136 bytes)
2011[NET] received packet: from 202.104.136.206[32783] to 192.241.216.55[500] (380 bytes)
2111[ENC] parsed ID_PROT request 0 [ KE No NAT-D NAT-D ]
2211[IKE] remote host is behind NAT
2311[ENC] generating ID_PROT response 0 [ KE No NAT-D NAT-D ]
2411[NET] sending packet: from 192.241.216.55[500] to 202.104.136.206[32783] (396 bytes)
2506[NET] received packet: from 202.104.136.206[32788] to 192.241.216.55[4500] (108 bytes)
2606[ENC] parsed ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
2706[CFG] looking for XAuthInitPSK peer configs matching 192.241.216.55...202.104.136.206[10.0.44.27]
2806[CFG] selected peer config "ikev1"
2906[ENC] generating ID_PROT response 0 [ ID HASH ]
3006[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32788] (92 bytes)
3106[ENC] generating TRANSACTION request 264157638 [ HASH CPRQ(X_USER X_PWD) ]
3206[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32788] (92 bytes)
3314[IKE] sending retransmit 1 of request message ID 264157638, seq 1
3414[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32788] (92 bytes)
3507[NET] received packet: from 202.104.136.206[32788] to 192.241.216.55[4500] (108 bytes)
3607[ENC] parsed TRANSACTION response 264157638 [ HASH CPRP(X_USER X_PWD) ]
3707[IKE] XAuth authentication of 'wbuntu' successful
3807[ENC] generating TRANSACTION request 4214691042 [ HASH CPS(X_STATUS) ]
3907[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32788] (92 bytes)
4016[NET] received packet: from 202.104.136.206[32788] to 192.241.216.55[4500] (92 bytes)
4116[ENC] parsed TRANSACTION response 4214691042 [ HASH CPA(X_STATUS) ]
4216[IKE] IKE_SA ikev1[1] established between 192.241.216.55[192.241.216.55]...202.104.136.206[10.0.44.27]
4316[IKE] scheduling reauthentication in 3307s
4416[IKE] maximum IKE_SA lifetime 3487s
4514[NET] received packet: from 202.104.136.206[32788] to 192.241.216.55[4500] (188 bytes)
4614[ENC] unknown attribute type (28683)
4714[ENC] parsed TRANSACTION request 3752970477 [ HASH CPRQ(ADDR MASK DNS NBNS EXP VER U_BANNER U_DEFDOM U_SPLITDNS U_SPLITINC U_LOCALLAN U_PFS U_SAVEPWD U_FWTYPE U_BKPSRV (28683)) ]
4814[IKE] peer requested virtual IP %any
4914[CFG] assigning new lease to 'wbuntu'
5014[IKE] assigning virtual IP 10.0.0.1 to peer 'wbuntu'
5114[ENC] generating TRANSACTION response 3752970477 [ HASH CPRP(ADDR DNS DNS) ]
5214[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32788] (108 bytes)
5308[NET] received packet: from 202.104.136.206[32788] to 192.241.216.55[4500] (300 bytes)
5408[ENC] parsed QUICK_MODE request 3228042318 [ HASH SA No ID ID ]
5508[IKE] received 3600s lifetime, configured 1200s
5608[ENC] generating QUICK_MODE response 3228042318 [ HASH SA No ID ID ]
5708[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32788] (188 bytes)
5805[NET] received packet: from 202.104.136.206[32788] to 192.241.216.55[4500] (76 bytes)
5905[ENC] parsed QUICK_MODE request 3228042318 [ HASH ]
6005[IKE] CHILD_SA ikev1{1} established with SPIs cd5fee60_i 0d2a931b_o and TS 0.0.0.0/0 === 10.0.0.1/32
2)IKEv2(EAP-MSCHAPv2)
客户端配置
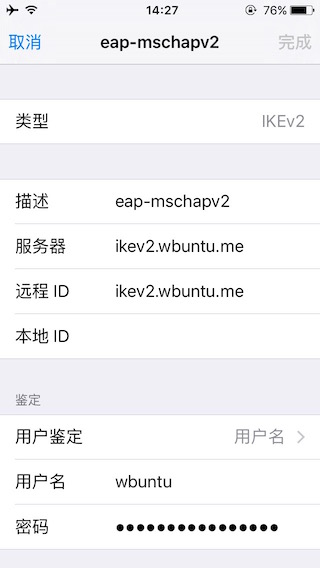
服务端连接日志
113[NET] received packet: from 202.104.136.206[32773] to 192.241.216.55[500] (604 bytes)
213[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ]
313[IKE] 202.104.136.206 is initiating an IKE_SA
413[IKE] remote host is behind NAT
513[IKE] sending cert request for "C=CH, O=Wbuntu, CN=Wbuntu CA"
613[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(MULT_AUTH) ]
713[NET] sending packet: from 192.241.216.55[500] to 202.104.136.206[32773] (465 bytes)
810[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (512 bytes)
910[ENC] parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) N(MOBIKE_SUP) IDr CPRQ(ADDR DHCP DNS MASK ADDR6 DHCP6 DNS6) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr ]
1010[CFG] looking for peer configs matching 192.241.216.55[ikev2.wbuntu.me]...202.104.136.206[10.0.44.27]
1110[CFG] selected peer config 'ikev2-eap-mschapv2'
1210[IKE] initiating EAP_IDENTITY method (id 0x00)
1310[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
1410[IKE] peer supports MOBIKE
1510[IKE] authentication of 'ikev2.wbuntu.me' (myself) with RSA signature successful
1610[IKE] sending end entity cert "C=CH, O=Wbuntu, CN=ikev2.wbuntu.me"
1710[ENC] generating IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ]
1810[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (1216 bytes)
1911[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (96 bytes)
2011[ENC] parsed IKE_AUTH request 2 [ EAP/RES/ID ]
2111[IKE] received EAP identity 'wbuntu'
2211[IKE] initiating EAP_MSCHAPV2 method (id 0x9B)
2311[ENC] generating IKE_AUTH response 2 [ EAP/REQ/MSCHAPV2 ]
2411[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (112 bytes)
2507[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (144 bytes)
2607[ENC] parsed IKE_AUTH request 3 [ EAP/RES/MSCHAPV2 ]
2707[ENC] generating IKE_AUTH response 3 [ EAP/REQ/MSCHAPV2 ]
2807[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (144 bytes)
2912[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (80 bytes)
3012[ENC] parsed IKE_AUTH request 4 [ EAP/RES/MSCHAPV2 ]
3112[IKE] EAP method EAP_MSCHAPV2 succeeded, MSK established
3212[ENC] generating IKE_AUTH response 4 [ EAP/SUCC ]
3312[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (80 bytes)
3411[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (112 bytes)
3511[ENC] parsed IKE_AUTH request 5 [ AUTH ]
3611[IKE] authentication of '10.0.44.27' with EAP successful
3711[IKE] authentication of 'ikev2.wbuntu.me' (myself) with EAP
3811[IKE] IKE_SA ikev2-eap-mschapv2[1] established between 192.241.216.55[ikev2.wbuntu.me]...202.104.136.206[10.0.44.27]
3911[IKE] scheduling reauthentication in 3414s
4011[IKE] maximum IKE_SA lifetime 3594s
4111[IKE] peer requested virtual IP %any
4211[CFG] assigning new lease to 'wbuntu'
4311[IKE] assigning virtual IP 10.0.0.1 to peer 'wbuntu'
4411[IKE] peer requested virtual IP %any6
4511[IKE] no virtual IP found for %any6 requested by 'wbuntu'
4611[IKE] CHILD_SA ikev2-eap-mschapv2{1} established with SPIs c87305fb_i 0b52a3e5_o and TS 0.0.0.0/0 === 10.0.0.1/32
4711[ENC] generating IKE_AUTH response 5 [ AUTH CPRP(ADDR DNS DNS) SA TSi TSr N(AUTH_LFT) N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_6_ADDR) ]
4811[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (288 bytes)
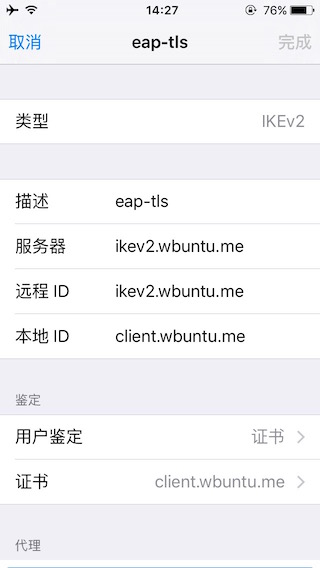
3)IKEv2(EAP-TLS)
客户端配置
服务端连接日志
113[NET] received packet: from 202.104.136.206[32780] to 192.241.216.55[500] (604 bytes)
213[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ]
313[IKE] 202.104.136.206 is initiating an IKE_SA
413[IKE] remote host is behind NAT
513[IKE] sending cert request for "C=CH, O=Wbuntu, CN=Wbuntu CA"
613[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(MULT_AUTH) ]
713[NET] sending packet: from 192.241.216.55[500] to 202.104.136.206[32780] (465 bytes)
809[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (512 bytes)
909[ENC] parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) N(MOBIKE_SUP) IDr CPRQ(ADDR DHCP DNS MASK ADDR6 DHCP6 DNS6) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr ]
1009[CFG] looking for peer configs matching 192.241.216.55[ikev2.wbuntu.me]...202.104.136.206[client.wbuntu.me]
1109[CFG] selected peer config 'ikev2-eap-tls'
1209[IKE] initiating EAP_IDENTITY method (id 0x00)
1309[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
1409[IKE] peer supports MOBIKE
1509[IKE] authentication of 'ikev2.wbuntu.me' (myself) with RSA signature successful
1609[IKE] sending end entity cert "C=CH, O=Wbuntu, CN=ikev2.wbuntu.me"
1709[ENC] generating IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ]
1809[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (1216 bytes)
1911[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (96 bytes)
2011[ENC] parsed IKE_AUTH request 2 [ EAP/RES/ID ]
2111[IKE] received EAP identity 'client.wbuntu.me'
2211[IKE] initiating EAP_TLS method (id 0x2E)
2311[ENC] generating IKE_AUTH response 2 [ EAP/REQ/TLS ]
2411[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (80 bytes)
2507[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (208 bytes)
2607[ENC] parsed IKE_AUTH request 3 [ EAP/RES/TLS ]
2707[TLS] negotiated TLS 1.0 using suite TLS_RSA_WITH_AES_128_CBC_SHA
2807[TLS] sending TLS server certificate 'C=CH, O=Wbuntu, CN=ikev2.wbuntu.me'
2907[TLS] sending TLS cert request for 'C=CH, O=Wbuntu, CN=Wbuntu CA'
3007[ENC] generating IKE_AUTH response 3 [ EAP/REQ/TLS ]
3107[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (1056 bytes)
3215[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (1104 bytes)
3315[ENC] parsed IKE_AUTH request 4 [ EAP/RES/TLS ]
3415[ENC] generating IKE_AUTH response 4 [ EAP/REQ/TLS ]
3515[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (80 bytes)
3610[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (1104 bytes)
3710[ENC] parsed IKE_AUTH request 4 [ EAP/RES/TLS ]
3810[IKE] received retransmit of request with ID 4, retransmitting response
3910[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (80 bytes)
4016[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (1104 bytes)
4116[ENC] parsed IKE_AUTH request 5 [ EAP/RES/TLS ]
4216[TLS] received TLS peer certificate 'C=CH, O=Wbuntu, CN=client.wbuntu.me'
4316[TLS] received TLS intermediate certificate 'C=CH, O=Wbuntu, CN=Wbuntu CA'
4416[ENC] generating IKE_AUTH response 5 [ EAP/REQ/TLS ]
4516[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (80 bytes)
4610[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (320 bytes)
4710[ENC] parsed IKE_AUTH request 6 [ EAP/RES/TLS ]
4810[CFG] using trusted ca certificate "C=CH, O=Wbuntu, CN=Wbuntu CA"
4910[CFG] checking certificate status of "C=CH, O=Wbuntu, CN=client.wbuntu.me"
5010[CFG] certificate status is not available
5110[CFG] reached self-signed root ca with a path length of 0
5210[CFG] using trusted certificate "C=CH, O=Wbuntu, CN=client.wbuntu.me"
5310[ENC] generating IKE_AUTH response 6 [ EAP/REQ/TLS ]
5410[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (144 bytes)
5511[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (80 bytes)
5611[ENC] parsed IKE_AUTH request 7 [ EAP/RES/TLS ]
5711[IKE] EAP method EAP_TLS succeeded, MSK established
5811[ENC] generating IKE_AUTH response 7 [ EAP/SUCC ]
5911[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (80 bytes)
6005[NET] received packet: from 202.104.136.206[32770] to 192.241.216.55[4500] (112 bytes)
6105[ENC] parsed IKE_AUTH request 8 [ AUTH ]
6205[IKE] authentication of 'client.wbuntu.me' with EAP successful
6305[IKE] authentication of 'ikev2.wbuntu.me' (myself) with EAP
6405[IKE] IKE_SA ikev2-eap-tls[1] established between 192.241.216.55[ikev2.wbuntu.me]...202.104.136.206[client.wbuntu.me]
6505[IKE] scheduling reauthentication in 3333s
6605[IKE] maximum IKE_SA lifetime 3513s
6705[IKE] peer requested virtual IP %any
6805[CFG] assigning new lease to 'client.wbuntu.me'
6905[IKE] assigning virtual IP 10.0.0.1 to peer 'client.wbuntu.me'
7005[IKE] peer requested virtual IP %any6
7105[IKE] no virtual IP found for %any6 requested by 'client.wbuntu.me'
7205[IKE] CHILD_SA ikev2-eap-tls{1} established with SPIs c0f2685b_i 0df61b30_o and TS 0.0.0.0/0 === 10.0.0.1/32
7305[ENC] generating IKE_AUTH response 8 [ AUTH CPRP(ADDR DNS DNS) SA TSi TSr N(AUTH_LFT) N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_6_ADDR) ]
7405[NET] sending packet: from 192.241.216.55[4500] to 202.104.136.206[32770] (288 bytes)
从连接日志可以看到,IKEv2和IKEv1的差别还是挺大的,但EAP-MSCHAPv2与EAP-TLS 的差别就主要集中在认证步骤上,后者有更严格的双向验证。
免证书的VPN
这里免证书的意思,还是指客户端免安装自签名的根证书,服务端仍旧需要配置。因为自签名的服务端和客户端证书需要对应的根证书来认证,所以客户端必须安装根证书。结果就是给一台机器配一个VPN,都需要安装一次根证书,如果因为一些原因,更换服务器域名或者根证书,就又需要下发一次,实在麻烦。
目前我的配置中除了使用IPSec VPN外,基本都需要证书。VPN的连接过程是一个双向认证的过程,与HTTPS的连接过程相似。在双方同时采用证书认证时,首先双方选择一套通用的加密算法,然后发送各自的证书,认证,建立连接。这些在上面的调试内容中都可以看到。所以~可以直接采用HTTPS证书来验证服务端,因为绝大多数客户端中已经内置了证书分发机构的根证书。
HTTPS证书的申请在这篇博客里有提到:折腾搬瓦工–07–搭建CAWServer的服务端
这里以StartSSL的证书为例,假如我们认证的域名还是ikev2.wbuntu.me,服务端证书选择适用于nginx的证书,命名为 ikev.wbuntu.crt,上传到 /etc/ipsec.d/certs目录,私钥为 ikev.wbuntu.pem,上传到 /etc/ipsec.d/private 目录。
修改ipsec.conf中的 ikev2-eap-mschapv2 配置,替换leftcert为 ikev.wbuntu.crt 然后修改ipsec.secrets,在首行新增一行,重启ipsec服务即可。
: RSA ikev.wbuntu.pem
虽然StartSSL的证书有效期可以长达一年,但由于它搞事,已经被许多厂商和谐了,推荐使用Let's Encrypt证书,有效期90天,可以配置自动更新证书后重启VPN服务端。
如果需要使用EAP-TLS,那么需要配置客户端证书,同样可以在StartSSL中申请一个,只不过在填写rightid时,需要使用自己认证的邮箱,Let's Encrypt目前没有提供生成客户端证书的服务。