使用WARP解除谷歌异常流量问题
文章目录
1. 前言
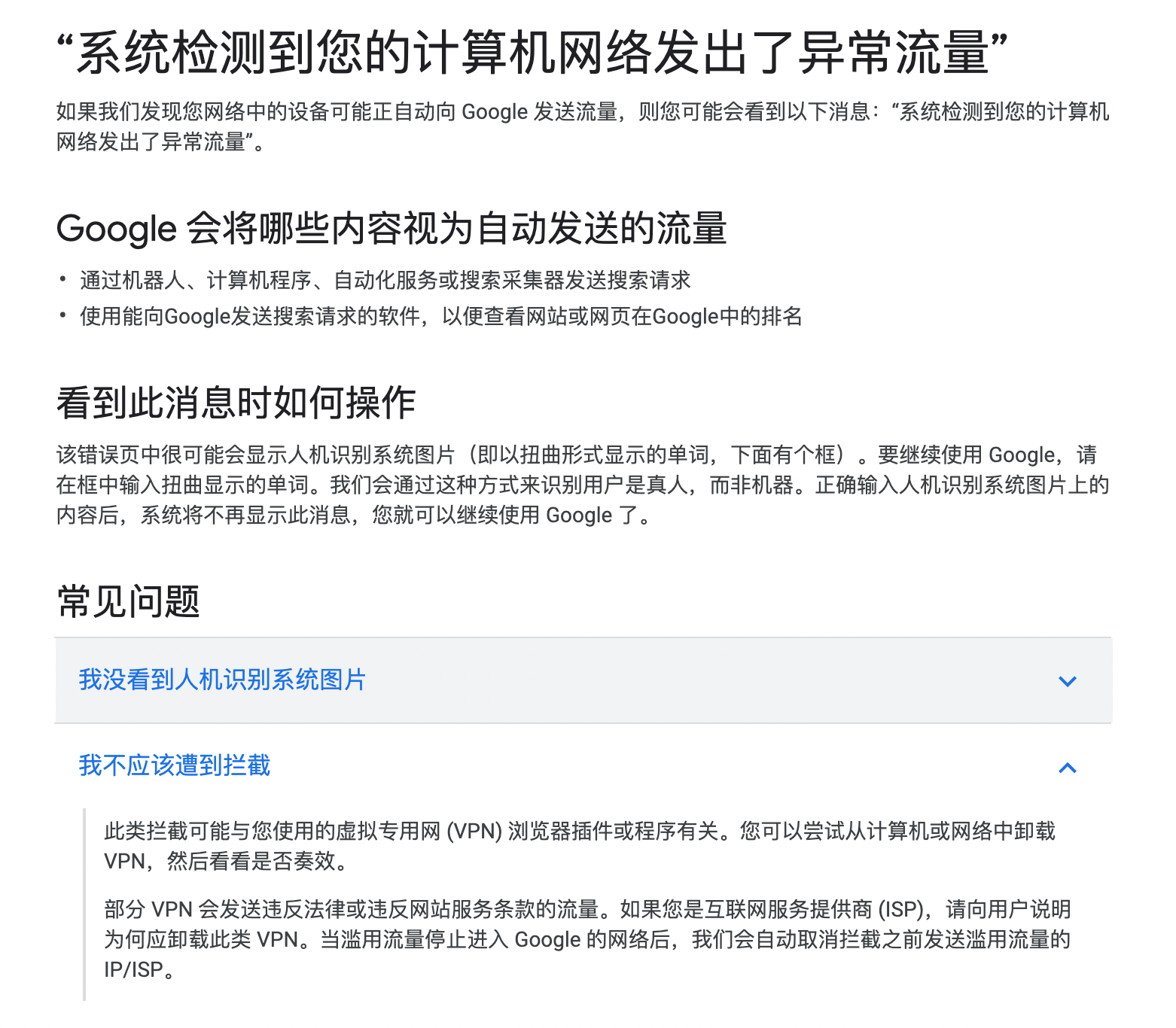
当你访问谷歌出现这个问题时,说明你的VPS或者代理的公网IP已经残废了90%,因为这个IP上了谷歌的黑名单且有99.99999%的概率无法解除,接下来每次你的谷歌搜索都会不定时出现人机验证页面,简直惨绝人寰。
2. 原因与解决思路
出现问题的原因如同截图里所说:
- 有爬虫或者其他程序通过该IP向谷歌发送搜索请求
- 滥用谷歌搜索功能
- 多人使用该IP作为代理访问谷歌
前两个原因通常是是第三个原因间接导致的,那么解决问题的思路也很明确:
- 更换IP:事实证明IP的更换速度跟不上谷歌封锁的速度
- 一人一个代理IP:每人一个专用代理服务器,代价过于昂贵
- 使用反向代理:将流量通过其他IP或者VPN二次转发
著名慈善企业cloudflare给了我们一个能彻底解决这个问题的方案:WARP,通俗点说就是免费的wireguard服务,最重要的是cloudflaret提供的出站IP不会被谷歌拉入黑名单,且能解锁许多针对IP进行限制的服务,例如Netflix。
3. 部署WARP
3.1 部署wireguard
这里不再赘述,都2021年了,许多Linux系统已经集成了对wireguard的支持,基本可以做到一键安装,详情参考wireguard官方文档:wireguard
3.2 部署wgcf
wgcf提供了自动化注册WARP与生成wireguard配置文件的功能,同样可一键安装:
1# 安装wgcf
2curl -fsSL git.io/wgcf.sh | bash
3# 注册WARP,生成WARP配置文件
4wgcf register
5# 通过WARP配置文件生成wireguard配置文件
6wgcf generate
执行完成后生成以下文件:
1# WARP配置文件
2wgcf-account.toml
3# wireguard配置文件
4wgcf-profile.conf
这里展示一个示例wireguard配置文件
1[Interface]
2PrivateKey = 4H5V4tIb7DsVI2CTkj/Nn8z/qDHLUAdgJFJTvUUMa1o=
3Address = 172.16.0.2/32
4Address = fd01:5ca1:ab1e:8aff:34bb:89c5:28d0:95e/128
5DNS = 1.1.1.1
6MTU = 1280
7[Peer]
8PublicKey = bmXOC+F1FxEMF9dyiK2H5/1SUtzH0JuVo51h2wPfgyo=
9AllowedIPs = 0.0.0.0/0
10AllowedIPs = ::/0
11Endpoint = engage.cloudflareclient.com:2408
3.4 配置wireguard
自动生成的wireguard配置文件中接管了IPv4与IPv6的路由,使用后会让VPS立刻断连。
我们的目的是让访问谷歌的流量走wireguard,其他的流量使用默认路由,这里就在三层利用路由策略来实现,假设VPS只有IPv4地址。
获取谷歌公网IP地址段
1#!/bin/sh
2STR=$(curl -s https://www.gstatic.com/ipranges/goog.json | grep ipv4Prefix | awk '{print $2}' | sed -e 's/"//g' | tr "\r\n" "," | sed 's/\r\n/,/g')
3CIDR=${STR%?}
4echo $CIDR
保存为脚本,执行后输出:
18.8.4.0/24,8.8.8.0/24,8.34.208.0/20,8.35.192.0/20,23.236.48.0/20,23.251.128.0/19,34.64.0.0/10,34.128.0.0/10,35.184.0.0/13,35.192.0.0/14,35.196.0.0/15,35.198.0.0/16,35.199.0.0/17,35.199.128.0/18,35.200.0.0/13,35.208.0.0/12,35.224.0.0/12,35.240.0.0/13,64.15.112.0/20,64.233.160.0/19,66.102.0.0/20,66.249.64.0/19,70.32.128.0/19,72.14.192.0/18,74.114.24.0/21,74.125.0.0/16,104.154.0.0/15,104.196.0.0/14,104.237.160.0/19,107.167.160.0/19,107.178.192.0/18,108.59.80.0/20,108.170.192.0/18,108.177.0.0/17,130.211.0.0/16,136.112.0.0/12,142.250.0.0/15,146.148.0.0/17,162.216.148.0/22,162.222.176.0/21,172.110.32.0/21,172.217.0.0/16,172.253.0.0/16,173.194.0.0/16,173.255.112.0/20,192.158.28.0/22,192.178.0.0/15,193.186.4.0/24,199.36.154.0/23,199.36.156.0/24,199.192.112.0/22,199.223.232.0/21,207.223.160.0/20,208.65.152.0/22,208.68.108.0/22,208.81.188.0/22,208.117.224.0/19,209.85.128.0/17,216.58.192.0/19,216.73.80.0/20,216.239.32.0/19
将上述IP地址替换默认配置文件的IPv4地址段,则新配置文件如下:
1[Interface]
2PrivateKey = 4H5V4tIb7DsVI2CTkj/Nn8z/qDHLUAdgJFJTvUUMa1o=
3Address = 172.16.0.2/32
4Address = fd01:5ca1:ab1e:8aff:34bb:89c5:28d0:95e/128
5DNS = 1.1.1.1
6MTU = 1280
7[Peer]
8PublicKey = bmXOC+F1FxEMF9dyiK2H5/1SUtzH0JuVo51h2wPfgyo=
9AllowedIPs = 8.8.4.0/24,8.8.8.0/24,8.34.208.0/20,8.35.192.0/20,23.236.48.0/20,23.251.128.0/19,34.64.0.0/10,34.128.0.0/10,35.184.0.0/13,35.192.0.0/14,35.196.0.0/15,35.198.0.0/16,35.199.0.0/17,35.199.128.0/18,35.200.0.0/13,35.208.0.0/12,35.224.0.0/12,35.240.0.0/13,64.15.112.0/20,64.233.160.0/19,66.102.0.0/20,66.249.64.0/19,70.32.128.0/19,72.14.192.0/18,74.114.24.0/21,74.125.0.0/16,104.154.0.0/15,104.196.0.0/14,104.237.160.0/19,107.167.160.0/19,107.178.192.0/18,108.59.80.0/20,108.170.192.0/18,108.177.0.0/17,130.211.0.0/16,136.112.0.0/12,142.250.0.0/15,146.148.0.0/17,162.216.148.0/22,162.222.176.0/21,172.110.32.0/21,172.217.0.0/16,172.253.0.0/16,173.194.0.0/16,173.255.112.0/20,192.158.28.0/22,192.178.0.0/15,193.186.4.0/24,199.36.154.0/23,199.36.156.0/24,199.192.112.0/22,199.223.232.0/21,207.223.160.0/20,208.65.152.0/22,208.68.108.0/22,208.81.188.0/22,208.117.224.0/19,209.85.128.0/17,216.58.192.0/19,216.73.80.0/20,216.239.32.0/19
10AllowedIPs = ::/0
11Endpoint = engage.cloudflareclient.com:2408
修改后的配置文件回通过添加路由规则,让IPv6的流量和所有访问谷歌IP的流量走wireguard。
拷贝配置文件到wireguard目录即可启用分流:
1cp wgcf-profile.conf /etc/wireguard/wgcf.conf
2systemctl enable --now wg-qucik@wgcf
4. 应用层分流
上述配置需要获取谷歌的IP段,然后加入到路由规则实现分流:
1➜ ~ ip route show
2default via 192.168.178.1 dev eth0 proto static metric 100
3172.17.0.0/16 dev docker0 proto kernel scope link src 172.17.0.1 linkdown
48.8.4.0/24 dev wgcf scope link
58.8.8.0/24 dev wgcf scope link
68.34.208.0/20 dev wgcf scope link
7......
8209.85.128.0/17 dev wgcf scope link
9216.58.192.0/19 dev wgcf scope link
10216.73.80.0/20 dev wgcf scope link
11216.239.32.0/19 dev wgcf scope link
假如我们还需要让Twitter、Facebook、Netflix等的流量走wireguard,则需要将他们的所有IP段都加入路由规则中,有点不太人道,那么我们就需要一个支持分流的代理软件,通过geoip或geosite的数据库实现应用层分流,让匹配规则的流量通过wireguard出站:
这里以常用科学上网工具为例,使用routing功能实现应用层分流,以下是服务端的配置文件示例,这里只展示出站规则与路由规则:
1{
2 "log": {
3 "loglevel": "warning"
4 },
5 "inbounds": [],
6 "outbounds": [
7 {
8 "protocol": "freedom",
9 "settings": {
10 "domainStrategy": "UseIPv4"
11 },
12 "tag": "direct"
13 },
14 {
15 "protocol": "freedom",
16 "settings": {
17 "domainStrategy": "UseIPv6"
18 },
19 "tag": "wgcf"
20 },
21 {
22 "protocol": "blackhole",
23 "settings": {},
24 "tag": "blackhole"
25 }
26 ],
27 "routing": {
28 "rules": [
29 {
30 "type": "field",
31 "outboundTag": "blackhole",
32 "protocol": ["bittorrent"]
33 },
34 {
35 "type": "field",
36 "outboundTag": "wgcf",
37 "domains": [
38 "geosite:google"
39 ]
40 }
41 ],
42 "balancers": []
43 }
44}
配置文件定义了三个出站规则:
- direct:使用IPv4解析域名,通过默认公网IP出站
- wgcf:使用IPv6解析域名,通过wireguard出站
- blackhole:禁止出站
然后定义了两个路由规则:
- 禁止种子流量
- 匹配谷歌站点,使用wgcf出站规则,走wireguard出站
这里还未解决原路返回的问题,依旧受限于系统路由规则,假如在wgcf出站规则中设置sendThrough使用wireguard的IPv4地址,仍然会走默认公网IP出站。
参考链接: